5 min read
Healthcare Cybersecurity: Taking a Proactive Approach
Performance Health Partners
May 1, 2023

Healthcare cybersecurity is more critical than ever before with the rise of technology, making patient data more vulnerable than ever to cyberattacks. Here are ways healthcare organizations can take a proactive approach to protecting sensitive healthcare data.
The healthcare industry has experienced a digital transformation over the past few years, with an increasing number of healthcare organizations relying on technology to deliver quality care. While there are countless benefits to this technology, innovation also carries risks.
As a result, healthcare cybersecurity is increasingly important as cybercriminals seek to exploit vulnerabilities in healthcare systems to access or steal sensitive patient information. Consequently, it is imperative that healthcare organizations take a proactive approach to cybersecurity to protect themselves from cyber threats and protect patient information. Read on for a list of strategies to start implementing now.
Types of Healthcare Cybersecurity Attacks
Cybersecurity threats pose a serious threat to healthcare organizations, as the sensitive and personal information they store can be extremely valuable to cybercriminals. In recent years, healthcare has become a major target of cyberattacks, and criminals use a variety of techniques to obtain access to systems and information.
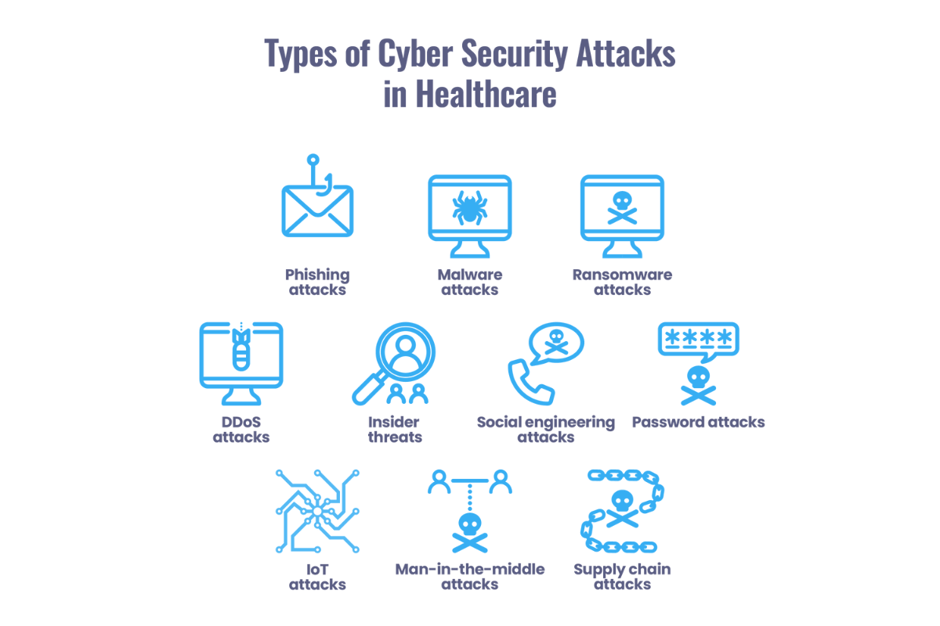
Some of the most common types of healthcare cybersecurity attacks include:
- Phishing attacks: Cyber criminals use emails or messages to trick users into revealing sensitive information or downloading malware.
- Malware attacks: Malicious software designed to damage, disrupt or gain unauthorized access to a system or network.
- Ransomware attacks: A type of malware that encrypts data and demands payment in exchange for the decryption key.
- DDoS attacks: A cyber attack where an overwhelming amount of traffic is sent to a server or network, causing it to crash or become unavailable.
- Insider threats: Employees or insiders with authorized access to a system or network intentionally or unintentionally cause harm or leak sensitive data.
- Social engineering attacks: Cyber criminals use manipulation or deception to trick users into revealing sensitive information or performing a specific action.
- Password attacks: Cyber criminals use automated software to guess passwords or use stolen passwords to gain access to a system or network.
- IoT attacks: Cyber criminals exploit vulnerabilities in internet-connected devices, such as medical devices, to gain access to a network.
- Man-in-the-middle attacks: Cyber criminals intercept and modify communication between two parties to steal sensitive data or gain unauthorized access to a system or network.
- Supply chain attacks: Cyber criminals target third-party vendors or suppliers to gain access to a healthcare organization.
Examples of Healthcare Cybersecurity Attacks
Unfortunately, cybersecurity attacks on healthcare organizations are becoming increasingly more common. Recent attacks making headlines include:
- Lehigh Valley Health Network (LVHN) ransomware attack: In February 2023, Lehigh Valley Health Network was the victim of a ransomware attack by BlackCat, a group known to be associated with Russia. The attackers released patient information and clinical images online and demanded a ransom payment, which LVHN refused to pay. The incident is being investigated with the help of law enforcement and cybersecurity experts. A hospital spokesman said that LVHN expects, “this shameful tactic to continue.”
- Anthem data breach: In 2015, health insurer Anthem experienced a massive data breach that exposed the personal information of some 80 million people. The breach was the result of a sophisticated cyberattack that targeted the company’s database, which contained sensitive personal information such as names, social security numbers, and medical IDs. The impact of the breach was far-reaching, with individuals' personal information being sold on the black market and used for identity theft and other fraudulent activities.
- Hollywood Presbyterian Medical Center ransomware attack: In February 2016, Hollywood Presbyterian Medical Center in Los Angeles was hit by a ransomware attack that resulted in a week-long disruption to critical healthcare services. The attackers ordered a ransom payment of $17,000 in bitcoin in exchange for restoring access to the hospital's systems. The attack forced the hospital to revert to paper-based systems and transfer patients to other hospitals for critical care.
- University of Vermont Health Network cyberattack: In October 2020, the University of Vermont Health Network experienced a cyberattack that affected its electronic medical record (EMR) systems and disrupted critical healthcare services. The attack was the result of a ransomware attack that was initiated after an employee opened a personal email on a company laptop while on vacation. It impacted multiple hospitals within the network, and the attackers demanded a ransom payment to restore access to the network's systems.
These real-life examples highlight the growing threat of cyberattacks in healthcare, which can result in the loss of critical health data, increased costs related to responding to cyber threats, and the potential harm to patient safety. They also bring to light the increasing need for robust cybersecurity measures to protect patient data and critical healthcare services.
5 Steps to Protect Patient Data
Unfortunately, healthcare tends to be more reactive than proactive when it comes to cybersecurity, according to findings outlined in the Healthcare Cybersecurity Benchmarking Study, published by KLAS Research and the American Hospital Association (AHA).
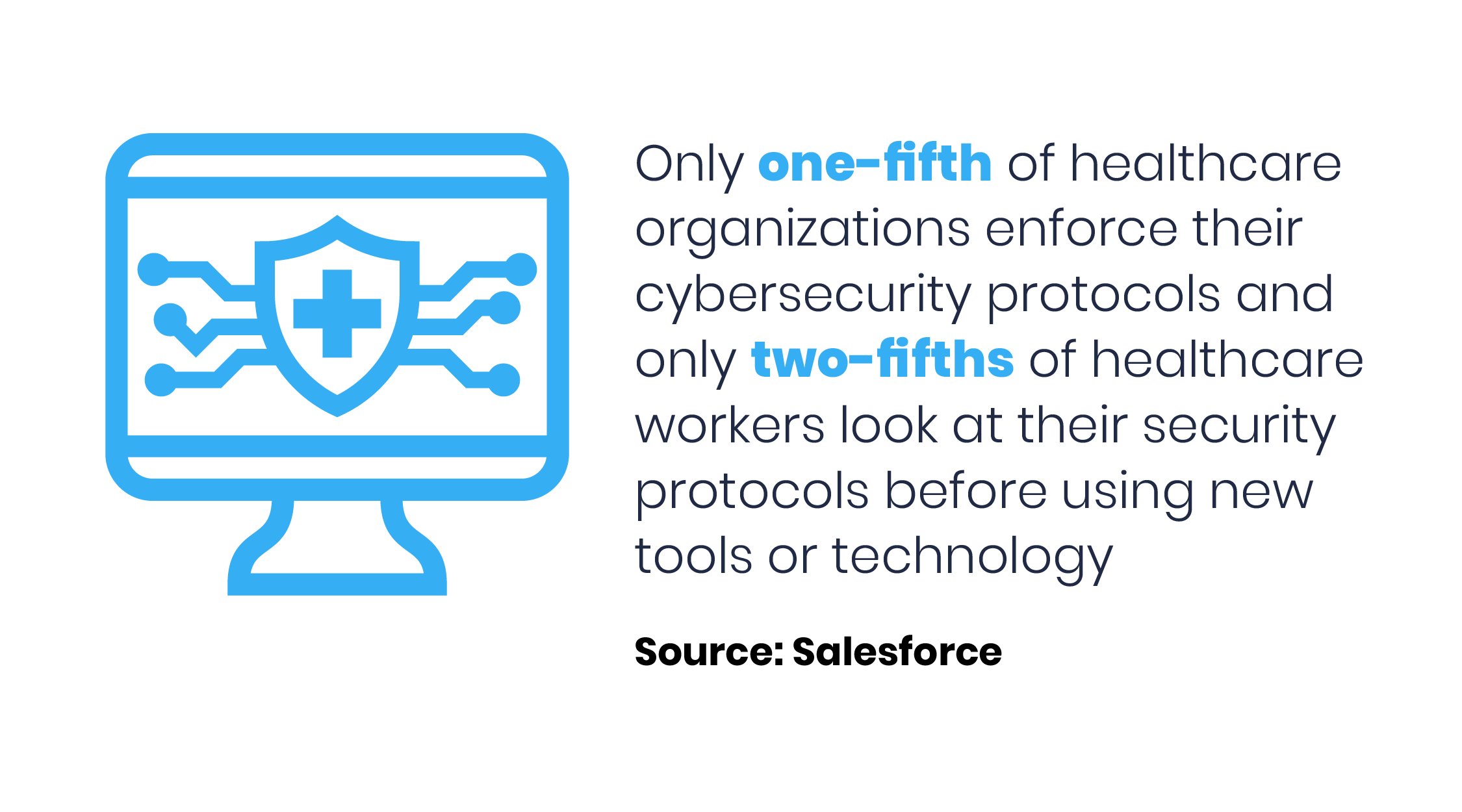
Another study released by Salesforce found that only one-fifth of healthcare organizations enforce their cybersecurity protocols and only two-fifths of healthcare workers look at their security protocols before using new tools or technology, even within organizations that have a security-first culture.
As healthcare organizations continue to rely on technology to deliver high quality care, it's critical that they remain vigilant and take a more proactive approach to protect against cyber threats. Below are five essential steps that healthcare organizations can take to improve their cybersecurity posture and protect patient data.
- Conduct regular security risk assessments: Security risk assessments are an important first step in identifying vulnerabilities in healthcare systems and developing an effective cybersecurity strategy. Healthcare organizations should regularly assess their security risks to identify potential weaknesses and take proactive steps to address them. This includes assessing network security, physical security, and access controls to ensure that patient data is protected from unauthorized access.
- Implement strong password policies: Weak passwords are a common entry point for cyber attackers looking to gain access to healthcare systems. Healthcare organizations can mitigate this risk by implementing strong password policies that require more complex passwords and frequent password changes. Additionally, multi-factor authentication can add an extra layer of protection by requiring users to provide additional verification before accessing sensitive data.
- Train staff on cybersecurity best practices: Healthcare staff play a critical role in maintaining the security of patient data. By training staff on cybersecurity best practices, such as identifying phishing emails and reporting suspicious activity, healthcare organizations can reduce the risk of successful cyberattacks. Ongoing training is essential to ensure that staff stay up-to-date with the latest threats and security best practices. Experts recommend providing training in smaller doses, more frequently; think three- to six-minute training installments highlighting best practices every couple weeks.
- Develop and test incident response plans: Should a cyberattack occur, healthcare organizations need to have a plan in place to respond swiftly and effectively. Incident response plans should include clear protocols for reporting and containing cyberattacks, as well as strategies for restoring systems and data. Regular testing of incident response plans can help healthcare organizations identify gaps in their cybersecurity strategy and make necessary improvements, while utilizing an incident management technology solution can facilitate the incident management process.
- Consistently update and patch systems: Outdated software and systems can leave healthcare organizations at an increased risk for cyberattacks. Regularly updating and patching systems is a simple yet effective way to reduce the risk of successful attacks. Furthermore, implementing automatic software updates can ensure that systems are always up-to-date and protected against the latest threats.
With the healthcare sector becoming more dependent on technology, cyber threats are an unfortunate reality that cannot be ignored. It’s imperative that organizations take a proactive approach to cybersecurity in healthcare by implementing robust security protocols and staying current with industry standards and regulations. Waiting to address cybersecurity risks isn’t an option.
Regular security audits, risk assessments, and vulnerability testing can help identify potential flaws in the system before cybercriminals exploit them. The stakes are high, and healthcare organizations must act now to protect their patients' privacy and secure their data from cyberattacks.
Ready to learn more?
Looking to enhance your organization's cybersecurity posture and identify potential gaps in your security processes? Performance Health Partners' incident management system can help. With our innovative platform, your organization can track and document cyber risks, and take corrective action to minimize the risk of data breaches and safeguard sensitive information.
With Performance Health Partners, you can take a preemptive approach to cybersecurity, preventing potential threats before they happen. Contact us today to learn more about how we can help bolster your cybersecurity processes.


